In the need for privacy (with bad or good intentions), people search for tools that can provide anonymous communication online. Tor is well known for that and have existed for a long time as a respected network of multiple layers of hops and encryption (“onion rings”). Just found this interesting article from Aaron M. Johnson et.al. where they have exploited vulnerabilities in Tor network by using traffic correlation attacks. Continue reading “Tor’s problem; Traffic Correlation Attacks”
In the need for privacy (with bad or good intentions), people search for tools that can provide anonymous communication online. Tor is well known for that and have existed for a long time as a respected network of multiple layers of hops and encryption (“onion rings”). Just found this interesting article from Aaron M. Johnson et.al. where they have exploited vulnerabilities in Tor network by using traffic correlation attacks. Continue reading “Tor’s problem; Traffic Correlation Attacks”
A street in Oslo where all traces disappear
Check if your Dropbox password is leaked…
e.g, at pastebin. I don´t support and encourage the BTC donations.
Smartphones with Full Encryption by Default
 iOS 8 has, and the next Android L will have, encryption of user data on device level as default. Android have provided this as an option for a while. iOS as well, but with decryption keys accessible outside the device. Continue reading “Smartphones with Full Encryption by Default”
iOS 8 has, and the next Android L will have, encryption of user data on device level as default. Android have provided this as an option for a while. iOS as well, but with decryption keys accessible outside the device. Continue reading “Smartphones with Full Encryption by Default”
If you haven’t already, check if your password is leaked…
As it seams, vulnerable websites and eCommerce sites with, e.g., plaintext user and password databases have been exploited.
Updated June 2016; https://haveibeenpwned.com/
Cryptocat Minilock, can crypto be that simple?
If you Google “decryotocat” you might not trust minilock as it has been developed by the same provider. Yet, minilock remains to released and will it break?
Read what wired has to say.
Explore Android as a Security Test Platform
I have previously blogged about the mobile pentest toolkit zANTI. They have a new version out with a handy GUI. This I use for proof-of-concept in private just to help my friends and family to get a better security mindset, e.g., how vulnerable you are on an open WIFI network. But there are more tools out there…
Continue reading “Explore Android as a Security Test Platform”
Free Security Test Tools from Rapid7
Rapid7 offers a set of free security/penetration test tools for free, e.g., including Metasploit framework and mobilisafe. Check it out here.
NSA of Things using Hardware Implants, Exploits, etc…
What to expect from a standard USB cable?
Probably not surprising, but check out this video from Chaos Communication Congress and the presentation “To Protect and Infect” by Jacob Applebaum to learn more about the speculations of NSAs hardware implants in USB cables, exploits, malware etc. for surveillance, namely: Somberknave, Totechaser, Iratemonk, Monkeycalendar (with references to Karsten Nohls work), Bulldozer, Iron Chef, Cottonmouth, Howlermonkey, CTX4000 (ragemaster RF-flooding) and more.
More about the actual documents presented you find here at Leaksource.
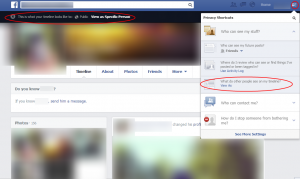
Limit public access to your Facebook profile
Facebook is changing and so is their Privacy Policy.
Some nice features exist limit access to your profile, photos etc. However, keep in mind that Cover Photos cannot be hidden, unless deleted. Access to Profile Picture can be limited, but the thumbnail will remain visible. Please see my old post on Social Media Permissions here:
Following are examples of how the features work.
View As:
Continue reading “Limit public access to your Facebook profile”