Among the banned companies are the consumer oriented Huawei and now Xiaomi. Read the lists from DOD.
Dark Web Exposure Test Service
ImmuniWeb released a new free tool to test, monitor and measure your website and domain exposure on the Dark Web.
Just tested mine, seems ok.
CSA tools, not just useful for cloud
 The CSA tools are useful not just for cloud, however ideal, but for cyber security in general.
The CSA tools are useful not just for cloud, however ideal, but for cyber security in general.
- Cloud Controls Checklist, a set of principles that cannot be argued
- Consensus Assessment Initiative, the questionnaire
- CSA STAR Registry, and the list of registered entities
- CSA Research
IAM before password vaults takes you
Security I believe is not to be fixed with tools only. Theres no silver bullet, so argumenting password vaults will fit all is unfortunate. For personal use I love both Googles Smart Lock and other password vaults. However, if you aim to control access to large sets of corporate services and apps, aim for SSO and complete IAM to prevent, detect and respond. This article adress this challenge well.
Filter Spam or Detect Spammers with Alias in Gmail
Had to share this as I´m getting tired of companies selling out my email to advertisers, leaked to spammers or them starting to spam my inbox just because I once registered on their service. So by adding a company-specific string to your email-address you can filter all spam and identify the origin of who sold out your address. E.g., I tested this when buying a travel ticket. Upon registration I did not provide them with my original email-address (myadr@gmail.com), but rather an address specifically crafted for this travel service agency (myadr+travelservicex@gmail.com). I will still receive the emails from the company, but also filter out its origin, even if they shared it with cooperating companies or advertisers.
Windows 10 Telemetry
Yesterday Microsoft blogged about their privacy journey, finally. It appears they have done improvements(?) to the privacy in Windows telemetry and “functional” reporting, and provided some custom privacy settings. Finally what I think is most interesting in this context is how to manage and utilize all this data for corporate security management, prevention and detection purposes. They claim to be “developing a set of analytics customized for your internal use” which sounds very interesting. However, it remains to see how and what they can offer. Upgrade Readiness is their first step.
So, there is a “basic level” and a full level?
Excited to hear more about how(if) this fits the GDPR.
Move away from the Perimeter
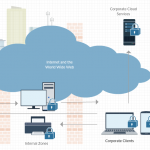 …Google says. Or they don’t actually say so, but their BeyondCorp approach to enterprise security certainly address it. Instead of building a perimeter sound enterprise network, they push security to whom shall access what without building a wall around it. I have tried to split this graphically in four as follows: Continue reading “Move away from the Perimeter”
…Google says. Or they don’t actually say so, but their BeyondCorp approach to enterprise security certainly address it. Instead of building a perimeter sound enterprise network, they push security to whom shall access what without building a wall around it. I have tried to split this graphically in four as follows: Continue reading “Move away from the Perimeter”
Mobile Trojans with SMS C&C
Looked into the Android SpySMS torjan as they say it has infected 40k users phones. This Mobile Trojan is using SMS as C&C protocol the way IRC C&C were used by PC Trojans back in the days. Got me thinking that the reliable SMS protocol is a nice protocol to control the android bots. The way this app try to block anti-virus from running and the long list of banking apps it controls is rather interesting as this has historically been more adapted by PC trojans and malware.
Facebook Security Education for Dummies
They do so by providing a Capture The Flag “hacking” challenge environment, open source (at Github) for everyone to play with. Might give it a go one time.
How not to do Information Security
 Nice blog post from Lenny Zeltser about mistakes to avoid working with Information Security. Most are probably obvious for many of you, but still… How many do just “Ban the use of external USB drives while not restricting outbound access to the Internet”? 🙂
Nice blog post from Lenny Zeltser about mistakes to avoid working with Information Security. Most are probably obvious for many of you, but still… How many do just “Ban the use of external USB drives while not restricting outbound access to the Internet”? 🙂
