Rapid7 offers a set of free security/penetration test tools for free, e.g., including Metasploit framework and mobilisafe. Check it out here.
NSA of Things using Hardware Implants, Exploits, etc…
What to expect from a standard USB cable?
Probably not surprising, but check out this video from Chaos Communication Congress and the presentation “To Protect and Infect” by Jacob Applebaum to learn more about the speculations of NSAs hardware implants in USB cables, exploits, malware etc. for surveillance, namely: Somberknave, Totechaser, Iratemonk, Monkeycalendar (with references to Karsten Nohls work), Bulldozer, Iron Chef, Cottonmouth, Howlermonkey, CTX4000 (ragemaster RF-flooding) and more.
More about the actual documents presented you find here at Leaksource.
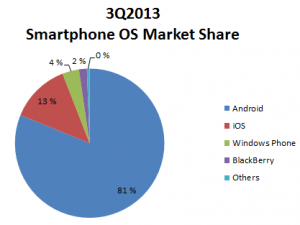
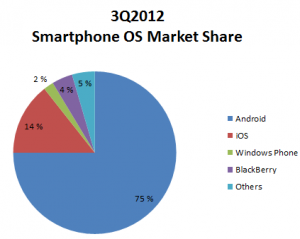
Android pushed past 80% market share for the first time in 3Q13
…According to IDC Quarterly Mobile Phone Tracker.
Below is a diagram of market share Q3 in 2013 and 2012 for illustrating the market growth og Android.
Optout of Android Ads, xapush, airpush etc…
Have you got annoying ads in your status bar or shortcuts on the home screen? Where do they come from and how can I remove/optout/delete them?
In Jelly Bean, you can figure out exactly which app caused a notification. By long-pressing it on the notification bar you can select App Info. From here you can actually disable notifications on a per-app basis altogether. Continue reading “Optout of Android Ads, xapush, airpush etc…”
“New” iPhone 5C and 5S
Me obviously being an Android fan, I just wanted to comment on the new iPhones 5C and 5S.
5C is to my opinion overpriced and has the look of iPhone 3GS (especially in white). Yes I know there is more inside, but enough said about 5C…
Now the new 5S. Continue reading ““New” iPhone 5C and 5S”
Check if you’re vulnerable to the Android “Master key” exploit
 Bluebox Security has released an App to check if your Android device is still vulnerable to the “master key” exploit. There is a patch out from Google, but not all handset providers have implemented it in their distros yet…
Bluebox Security has released an App to check if your Android device is still vulnerable to the “master key” exploit. There is a patch out from Google, but not all handset providers have implemented it in their distros yet…
Check out this article if you want to know more about this expoit.
http://bluebox.com/corporate-blog/bluebox-uncovers-android-master-key/
And this article about it being patched by Google.
http://www.engadget.com/2013/07/09/google-plugs-android-security-hole/
Control your Java
Recent Java vulnerabilities have made Security experts advice people to fully disable Java scripts, or use two browsers such as;
– one for less critical tasks with Java, and
– one for critical tasks (e.g., online banking) where Java is enabled only when needed
However, Google Chrome lets you disable, enable only exceptions where you what to run Java and Javascripts, or if you would like Java- “click and play”. Problem solved?:)
Alternatively use “click to play” as explained here: http://superuser.com/questions/201613/disable-java-plugin-in-google-chrome
Evaluate your site’s mobile-readiness
The mobiReady testing tool lets you easily test your mobile website for e.g.;
- Readiness
- Size
- Time
- Cost
- Visualization
- and other compliance tests
Playing with Anti
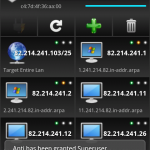
Just scanned X devices on my network using Android Network Toolkit (#ANTI3) by @zImperium Get it now: http://zimperium.com/anti.html
As you can see from the pictures, Anti is intuitive and simple to play with, and can as easily be used by security professionals as newbies. The screenshots was taking while using the open wireless network on flight from Oslo to Trondheim (flying Norwegian).
The app was used only to illustrate an example, where the sniffing was aimed at a friends smartphone (with his consent).
The sniffing screenshot is a good example of how easily adversaries can capture unencrypted traffic in open wireless networks.
Nmap6
Check out the new Nmap6! Looks great at first glance!
[snap url=http://www.theregister.co.uk/2012/05/25/nmap_6_released/ alt=”This snapshot has taken by Snap A Site”]