They say it will be discontinued in April. It’s rather sad, liked the initiative and how it made it simple to the ordinary IT user to update apps. Look for SUMo (Software Update Monitor), uCheck and more here for a replacement.
IAM before password vaults takes you
Security I believe is not to be fixed with tools only. Theres no silver bullet, so argumenting password vaults will fit all is unfortunate. For personal use I love both Googles Smart Lock and other password vaults. However, if you aim to control access to large sets of corporate services and apps, aim for SSO and complete IAM to prevent, detect and respond. This article adress this challenge well.
MS fighting ransomware
Windows have taken the effort to fight ransomware with Controlled Folder Access, bleepingcomputer sais. It requires Win 10 Fall Creators Update, which is version 1709. Check your version. Enable it under Virus & threat protection if available.
*playing with Windows settings URI, making the settings links.
PSnmap
Portscanning done “silently” using powershell does not require administrative privileges, thus being a tool where nmap (or similar tools) is no option (due to time and/or authorisation constraints).
The PSnmap tool utilise Powershell capabilities in its module for port scanning.
- Download package from Poweshelladmin
- Install module
Install-Module -Name PSnmap -Scope CurrentUser
- Check if module is installed
Get-Module -ListAvailable
- Set Execution Policy
Set-ExecutionPolicy -ExecutionPolicy RemoteSigned -Scope CurrentUser
- Import module
Import-Module -Name PSnmap
- Run scans, e.g.:
PSnmap -Cn 192.168.1.1 -ThrottleLimit 5 -Timeout 5 -PortConnectTimeoutMs 5 -Verbose > test.txt
To scan more stealth, adjust throttle limit (HIDS may detect resource intensive processes), and timeout values. See full list here.
Filter Spam or Detect Spammers with Alias in Gmail
Had to share this as I´m getting tired of companies selling out my email to advertisers, leaked to spammers or them starting to spam my inbox just because I once registered on their service. So by adding a company-specific string to your email-address you can filter all spam and identify the origin of who sold out your address. E.g., I tested this when buying a travel ticket. Upon registration I did not provide them with my original email-address (myadr@gmail.com), but rather an address specifically crafted for this travel service agency (myadr+travelservicex@gmail.com). I will still receive the emails from the company, but also filter out its origin, even if they shared it with cooperating companies or advertisers.
Windows 10 Telemetry
Yesterday Microsoft blogged about their privacy journey, finally. It appears they have done improvements(?) to the privacy in Windows telemetry and “functional” reporting, and provided some custom privacy settings. Finally what I think is most interesting in this context is how to manage and utilize all this data for corporate security management, prevention and detection purposes. They claim to be “developing a set of analytics customized for your internal use” which sounds very interesting. However, it remains to see how and what they can offer. Upgrade Readiness is their first step.
So, there is a “basic level” and a full level?
Excited to hear more about how(if) this fits the GDPR.
Kali for Azure
 I have been using/playing with Azure lately. Everything from server builds, Azure AD, network security and all those magical app services and microservices for AI, cognitive behaviour, threat analytics and more. Playing with Azure is free for a limited subscription with enough cash to play with most (although not resource intensive) services. See here.
I have been using/playing with Azure lately. Everything from server builds, Azure AD, network security and all those magical app services and microservices for AI, cognitive behaviour, threat analytics and more. Playing with Azure is free for a limited subscription with enough cash to play with most (although not resource intensive) services. See here.
Azure security enables you to protect, detect and respond your services. What I find even more interesting from a security perspective is how you can penetration test your Azure ser vices using Kali for Azure. Have not yet tested it out myself, but plan to. It can be acquired here.
Just make sure you let Microsoft know if you plan to pentest something – as you probably would if you tested your corporate network:)
Cyber Threat Awareness for CxOs
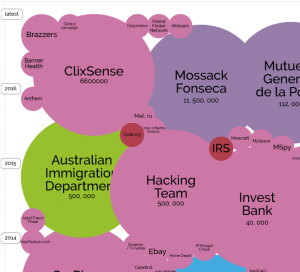 Information is Beautifull still propagate their “World’s Biggest Data Breaches” map. A great way to show why cyber security is important in means of both protection and detection. The worst are probably not even in this map…
Information is Beautifull still propagate their “World’s Biggest Data Breaches” map. A great way to show why cyber security is important in means of both protection and detection. The worst are probably not even in this map…
The Self-Healing Double Ratchet Algorithm
If you are looking into perfect forward secrecy (e.g., a compromised key for one message does not compromise all past messages) in exchange encrypted messages you should check out Double Ratchet Algorithm.
You can use Qualys to check if your site needs it.
IoT is taking over
People, and manufacturers apparently, does not care how their gadgets are secured. So makes a DDoS.
Check out how Mirai was used to exploit some Chinese DVRs and cameras.
