Have lately been playing around with Atomic Red Team open atomic tests and this is pretty good stuff, and easy to add value both to prevention, detection and respons. They are also integrated with LimaCharlie, which is worth checking out for detection and response.
Open Source alternatives, always
I like Open Source tools and the way it moves tech. Opensourcealternatives.to is in that case a rich source to finding alternatives to all those commercial tools you have to pay for even just for testing. E.g., Photoshop -> GIMP, Whatsapp -> Signal, Lastpass -> KeePassXC…
Israels ban of hacker tools
Reducing export to many countries, not Norway.
Wiki for Cloud Security
NotSoSecure have made this wiki for cloud security, with tools and methods for how to research and develop knowledge in this topic. I find it quite useful when browsing various cloud security research blogs they refer to, tools and methods. E.g., for AWS a lot of defensive and offensive tools are listed such as ScoutSuite in which I have great experience with.
MVSP: The bare minimum for B2B security
Minimum Viable Security Product has a baseline requirements list for B2B software and products thats worth checking out. It is founded on the same principle as most frameworks, e.g., as the CIS critical security controls, by “prioritizing security functions that are effective”.
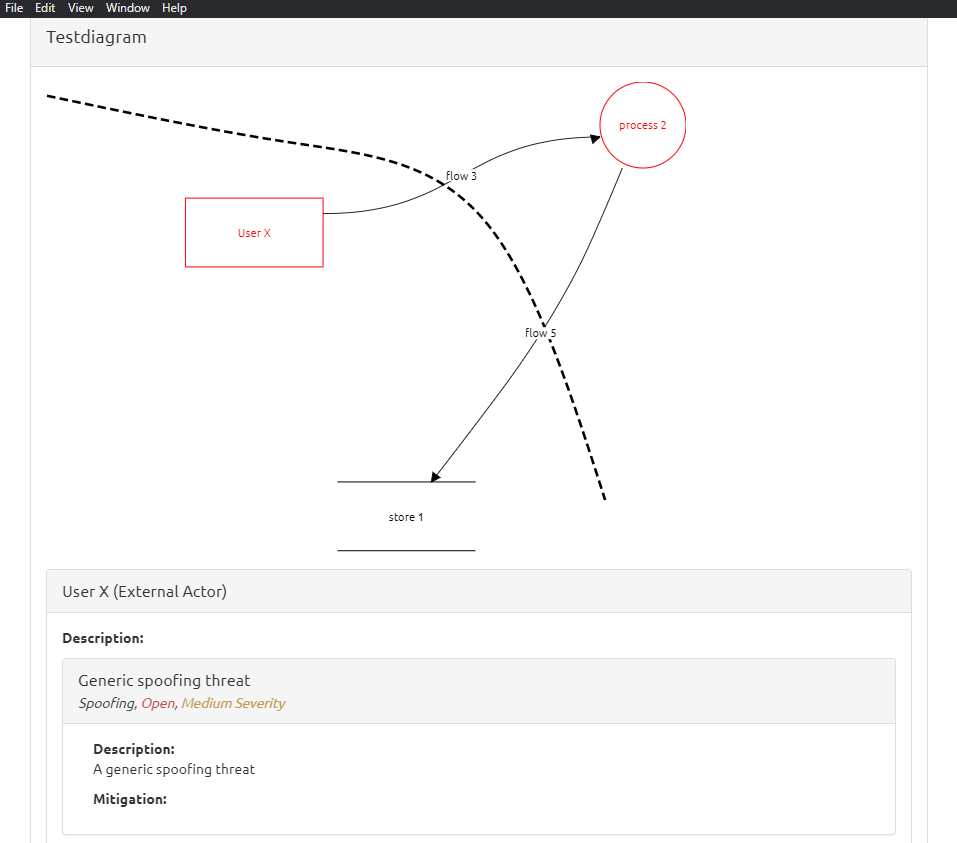
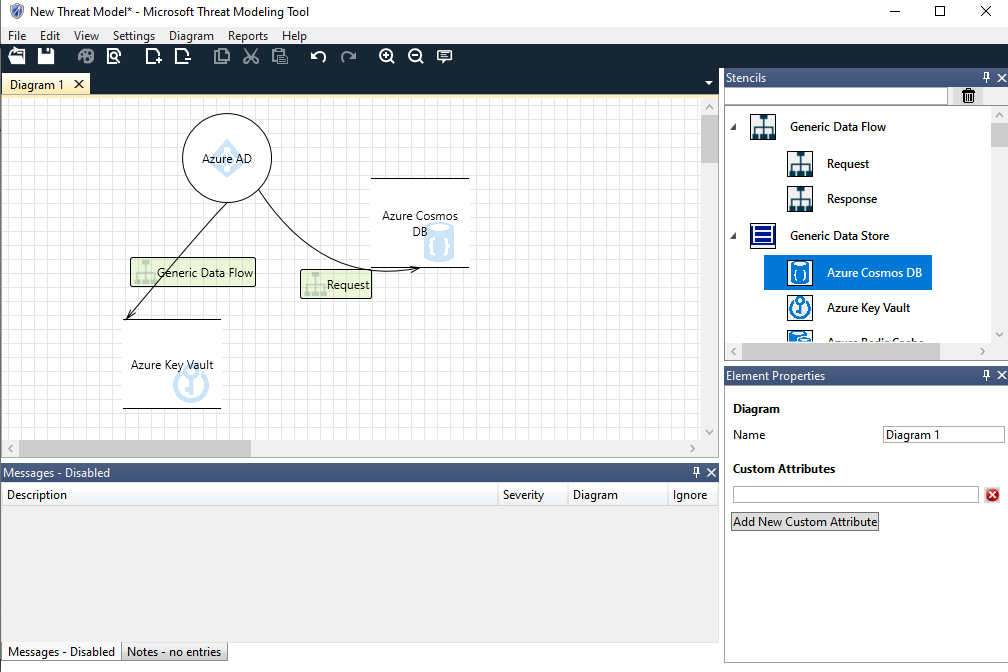
Threat Modeling Tools
MS Threat modeling tool, Cairis, Iriusrisk, Kenna, OWASP pytm, OWASP threat dragon, threagile are some of the most known threat modeling tools I know.
Personally I like OWASP Threat Dragon for being supported on most common platforms, and because of its flexibility in designing and registering threats. MS Threat modeling tool provides a lot of out-of-the-box threat scenarios with details based on the model designed.
Fingerprint that EDR for red team testing
EDRhunt, an open source, tool to detect installed EDR on Windows. Fingerprinting detection mechanisms obviously make the red team test even more sophisticated.
Practical use of 3D printer when you have a newborn
To protect my B&W speakers I had to design and print honeycomb covers. Workshop perfect!


Vulnerability scanners coverage is only half of published CVEs
Intruder has assessed the most know CVE vulnerability scanners on the market. One great fun fact is that they both cover only half the published CVEs. Check it out and whos the winner.
Drop EICAR in Azure
According to Microsoft it is encouraged to drop EICAR and to generate anomalous security logs in order to test security monitoring and detections in Azure… Wonder if that means their way og feeding their detection rules.
