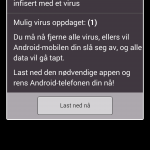
 Often I get ads for anti-virus for mobile in free Android apps with ads. This time a scam, claiming to be a Kaspersky antivirus scanner was presented. Obviously this was not a Kaspersky ad, as you can see in the following screenshots.
Often I get ads for anti-virus for mobile in free Android apps with ads. This time a scam, claiming to be a Kaspersky antivirus scanner was presented. Obviously this was not a Kaspersky ad, as you can see in the following screenshots.
Continue reading “Google in-app ads present fraudulent anti-malware”

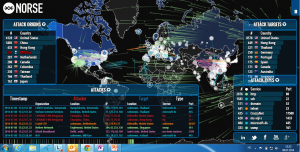 Norse has made an
Norse has made an  It is now 7 years since we did this bachelor thesis project, and it is nice to see the
It is now 7 years since we did this bachelor thesis project, and it is nice to see the